Industrial switches have become indispensable in modern industrial automation. Their robust interference resistance, reliability, and stability meet the communication demands of industrial automation, monitoring, and other fields. They connect, manage, and coordinate various devices and systems, providing a stable and efficient communication environment for industrial automation. When configuring industrial switches, attention must be paid to a series of key points to fully leverage their performance, security, and reliability. This article will focus on the important steps and considerations for industrial switch configuration to help optimize industrial networks.
IP Address Allocation and Subnetting
IP address allocation and subnetting for industrial switches are critical configuration steps, ensuring devices communicate correctly while maintaining logical independence. The following outlines the steps:
IP Address Allocation:
- Understand the network plan to determine the IP address range, subnet mask, gateway, etc.
- Select IP Address Range: Choose an unused IP address range based on the plan to avoid conflicts.
- Assign IP to Switch: Log in to the management interface and set the IP address for the switch's management interface.
- Configure Default Gateway: Set the default gateway, typically the IP address of the connected router or firewall.
Subnet Division:
- Determine Subnet Plan: Consider network layout, functional requirements, and security to determine the number of subnets and IP address needs.
- Select Subnet Mask: Choose a subnet mask based on the number of hosts to ensure sufficient IP addresses.
- Divide Subnets: Split the IP range according to the subnet mask to guarantee enough IP addresses for host usage.
- Associate VLANs and Subnets: Use VLANs to isolate devices, associating each VLAN with a specific subnet.
- Configure Routing: If cross-subnet communication is required, configure routers or Layer 3 switches to enable data forwarding.
- Test Connectivity and Communication: Verify that devices across different subnets can communicate with each other.
VLAN Configuration
Configuring VLANs logically groups devices, enhancing security and management efficiency while preventing broadcast storms.
- Log in to the management interface: Access the switch management interface via its IP address.
- Create a VLAN: Establish a new VLAN within the VLAN settings.
- Add a VLAN: Assign an ID and name to the VLAN.
- Associate Ports: Specify which ports belong to the VLAN, marked or unmarked.
- Configure VLAN Interfaces: Set up virtual interfaces for each VLAN, including IP addresses.
- Test Communication: Verify devices in different VLANs can communicate normally and test routing.
- Configure VLAN Tagging (Optional): Set up tagging when passing VLAN information between multiple switches.
- Save Configuration: Save and apply changes after completing setup.
Port Configuration
Configure rate limiting, duplex mode, flow control, and other settings for each port. Bandwidth throttling controls traffic flow to enhance network performance.
- Configure rate limits for specific scenarios, such as preventing excessive traffic from impacting performance.
- Ensure bandwidth requirements for critical applications while preventing non-critical applications from affecting performance.
- Limit broadcast storms to reduce network congestion and instability.
- Avoid resource exhaustion and maintain stable network operation.
- Provide a foundation for implementing QoS policies by setting different rates based on requirements.
STP/RSTP/MSTP Configuration
Spanning Tree Protocol (STP), Rapid Spanning Tree Protocol (RSTP), and Multiple Spanning Tree Protocol (MSTP) prevent loops and enhance network stability.
- STP: Slower convergence, suitable for simple networks.
- RSTP: Faster convergence, provides rapid loop detection.
- MSTP: More granular loop control, suitable for large networks.
When configuring STP/RSTP/MSTP, note these key details:
STP Configuration:
- Root Bridge Selection: Selecting the root bridge is a critical step in STP. Prioritize the switch with the lowest priority and MAC address as the root bridge to ensure the shortest path.
- Port Role Configuration: Switch ports have distinct roles, such as root ports, designated ports, and alternate ports. Ensure each switch port is correctly assigned its role.
- Port Cost Configuration: Set a cost value for each port, which influences the selection of root and designated ports. Ports with lower costs are more likely to become designated ports.
- Convergence Time: STP converges slowly, potentially causing network outages. Consider using alternative spanning tree protocols for faster convergence.
RSTP Configuration:
- Fast Convergence: RSTP provides rapid convergence, but network fluctuations caused by rapid switching of port roles and states still require attention.
- Dedicated Ports: RSTP introduces the concepts of dedicated ports and spare ports, eliminating the need for alternate ports and reducing unnecessary port state transitions.
MSTP Configuration:
- Instance Partitioning: MSTP allows partitioning into multiple instances, each capable of containing multiple VLANs. Ensure each instance's VLAN partitioning and instance ID are correctly configured.
- Root Bridge Selection: Each instance requires a root bridge. Ensure root bridge selection and priority settings are correct.
- Instance Association: Ensure VLANs are correctly associated with MSTP instances to achieve finer-grained loop control.
- Synchronized Configuration: MSTP configurations across multiple switches must be synchronized to maintain consistent loop control.
Common Considerations:
- Version Compatibility: Ensure switches support the selected STP version and maintain compatibility with other switches.
- Priority Settings: Switch priority settings influence root bridge selection and must be appropriately configured across the network.
- Single Protocol Selection: STP, RSTP, and MSTP are mutually exclusive. Select and configure one protocol to prevent conflicts.
- Regular Monitoring: After configuration, periodically monitor the STP status to ensure network health.
- Troubleshooting: During network failures, STP configuration and status should be considered as potential contributing factors.
By paying attention to these details, you can avoid common pitfalls when configuring STP, RSTP, and MSTP, establishing a stable network topology and effective loop control.
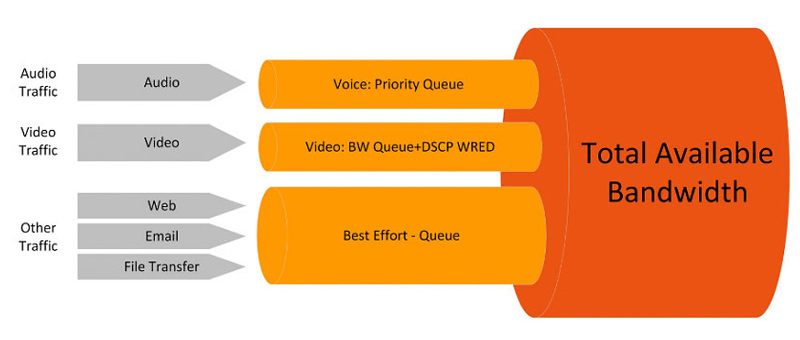
QoS Configuration
Configure QoS to ensure critical traffic receives priority bandwidth allocation and elevate the priority of real-time traffic.
- Determine traffic classification based on requirements, such as audio, video, and data.
- Identify traffic types using classification rules and set bandwidth limits.
- Configure queues and scheduling algorithms to manage different traffic categories.
- Test and optimize to ensure QoS achieves the desired results.
Security Configuration
- Enable port security, 802.1X authentication, and MAC address filtering to restrict device access.
- Configure ACLs to control inbound and outbound traffic, protecting the network from unauthorized access.
- Set rules for specific applications to meet compliance requirements.
Here we focus on configuring ACLs (Access Control Lists), which enhance network security by preventing unauthorized access and malicious traffic from disrupting normal operations. Exercise caution when configuring ACLs, adhering to security best practices. For industrial switches, pay particular attention to these critical considerations:
- Clear Policy Objectives: Before configuring ACLs, define your policy goals. Determine which traffic types to restrict and under what conditions to permit or deny traffic.
- Precise Rule Design: Design ACL rules with maximum precision to avoid unintended impacts. Specifically, include precise source and destination IP addresses, port numbers, protocol types, etc. in rules. Avoid overly broad wildcards to prevent legitimate traffic from being blocked.
- Rule Order: ACL rules are matched sequentially, making order critical. Place the most common rules first, followed by stricter and more specific rules. This ensures frequent traffic is matched and processed quickly.
- Firewall-like Policy: When designing ACLs, adopt a firewall-like approach by denying all traffic by default and adding allow rules as needed. This helps prevent unauthorized traffic from entering the network.
- Priority and Logging: Some industrial switches support setting priorities and logging options for ACL rules. Assign higher priorities to critical rules for preferential matching. Additionally, enabling logging helps track and analyze incoming and outgoing traffic.
- Testing and Validation: After configuring ACLs, thorough testing and validation are essential. Ensure rules function as intended without inadvertently blocking legitimate traffic or creating security vulnerabilities. Test ACL effectiveness using simulated or actual traffic.
- Backup and Recovery: Before making ACL configurations, back up the switch configuration. This allows you to restore to a previous working state if issues arise or configurations fail to meet expectations.
- Regular Review and Updates: Network environments and requirements may change over time. It is crucial to periodically review ACL rules and adjust or update them as necessary.
- Documentation and Annotations: Add clear annotations and documentation to ACL rules, explaining the purpose and intent of each rule. This helps other administrators understand the configuration and avoids confusion about rule objectives during future modifications.
Link Aggregation
Link Aggregation is a technology that combines multiple physical network links (ports) into a single logical link. It aims to increase bandwidth, provide redundancy, enhance reliability, and reduce the impact of single points of failure. This proves highly valuable in network environments with high load, high availability, and stringent redundancy requirements.
Managed switches play a critical role in this process. Guanglu Technology's managed industrial switches provide the following key features for link aggregation:
- Link Aggregation Configuration: Easily configure link aggregation to combine multiple physical links into a single logical link. Administrators can select which ports to aggregate and define load balancing and redundancy methods.
- Protocol Support: Managed switches support specific protocols essential for link aggregation, such as LACP or static aggregation, ensuring the combined links function correctly and enabling status monitoring.
- Status Monitoring: Monitors the status of aggregated links, including the activity status, bandwidth utilization, and faults of each physical link.
- Failover: Within a link aggregation group, if one physical link fails, other links automatically take over to maintain network connectivity.
- Performance Optimization: Load balancing policies can be configured based on actual requirements, distributing traffic evenly across multiple links to maximize bandwidth utilization.
- Remote Management: Administrators can configure and monitor link aggregation remotely without on-site presence, enhancing management efficiency and response speed.
Management and Monitoring
- Enable remote management protocols (e.g., SNMP) to monitor switch status.
- Configure logging for troubleshooting and auditing.
- Set up SSH access to encrypt remote management traffic.
- Perform regular configuration backups to prevent data loss.
Through these configurations, industrial networks can establish stable, efficient, and secure communication environments to meet the challenges of industrial automation. Each step plays a critical role in enhancing network performance, security, and reliability, requiring appropriate adjustments based on actual network requirements and hardware models.




